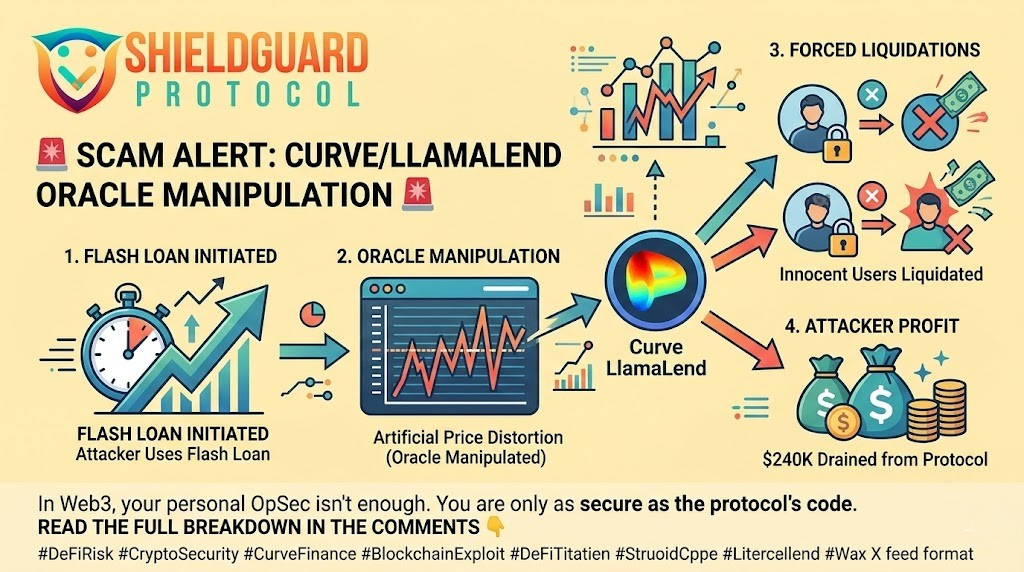
SCAM ALERT: The CrossCurve (EYWA) Bridge Exploit
SCAM ALERT: The CrossCurve (EYWA) Bridge Exploit
Severity: Critical 
What Happened?
In the early hours of February 2, 2026, the CrossCurve protocol (formerly known as EYWA) suffered a catastrophic security breach, resulting in the loss of approximately $1.44 Million in user funds.
This was not a simple phishing attack but a complex Smart Contract Logic Exploit that allowed attackers to “trick” the bridge into releasing funds without depositing anything.
 The Technical Breakdown (Simplified)
The Technical Breakdown (Simplified)
To understand how to protect yourself, you must understand the flaw. The attackers targeted two specific contracts:
- The Target:
PortalV2(The vault where user funds are locked). - The Flaw:
ReceiverAxelar(The messenger that tells the vault when to release funds).
The “Spoofed Message” Attack
Normally, when you bridge tokens, a secure “Oracle” (like a digital notary) confirms you actually deposited money on Chain A before releasing it on Chain B.
- The Vulnerability: The CrossCurve contract failed to verify who sent the message.
- The Exploit: Attackers sent a fake “I deposited funds” message directly to the
ReceiverAxelarcontract. Because the validation check was missing, the contract blindly trusted the message and orderedPortalV2to unlock real tokens to the hacker’s wallet.
ShieldGuard Analogy: Imagine a bank vault that opens for anyone who walks up and says, “The manager sent me,” without ever checking their ID badge.
 Immediate Action Required
Immediate Action Required
If you have ever used CrossCurve, EYWA, or their associated liquidity pools (on Curve Finance), take these steps immediately:
1. Pause All Interactions
Do not attempt to bridge funds, add liquidity, or swap using the CrossCurve interface until an official “Post-Mortem” and “Resumption of Service” is announced by the team.
2. Revoke “Unlimited” Approvals
Even if you don’t have funds in the bridge right now, your wallet might still have an “Unlimited Allowance” active. If the attackers find a way to exploit the deposit function, they could potentially drain your wallet of the approved tokens.
- Go to: Revoke.cash or Rabby Wallet’s “Approval” tab.
- Search for:
CrossCurve,EYWA, orPortalV2contracts. - Action: Click Revoke immediately.
3. Beware of “Refund” Scams
This is the most dangerous phase. Scammers are already deploying fake “CrossCurve Compensation” sites.
- The Lie: “Click here to check your eligibility for the $3M hack reimbursement.”
- The Reality: These sites are wallet drainers. The team has NOT announced a refund portal yet.
 ShieldGuard Learn: Prevention & Due Diligence
ShieldGuard Learn: Prevention & Due Diligence
How can you spot similar risks in the future? Use the “3-Point Bridge Safety Check”:
- The “Lindy Effect” of Code:
New bridges are high-risk. CrossCurve recently rebranded from EYWA. Rebrands often come with new contract migrations that haven’t been battle-tested as long as established protocols like Uniswap or Aave.
Tip: Wait 3–6 months after a major protocol upgrade before depositing significant capital.
2.Monitor “TVL” Deviations:
If a bridge’s Total Value Locked (TVL) drops by 99% in minutes (as CrossCurve’s did), it is a red flag. Use tools like DefiLlama to set alerts for sudden TVL drops on protocols you use.
3.Diversify Bridge Usage:
Never keep all your cross-chain liquidity in one protocol. If you must bridge large amounts, split it into smaller chunks or use multiple bridges (e.g., Stargate, Across, Hop) to minimize the impact of a single exploit.

 SCAM ALERT: The CrossCurve (EYWA) Bridge Exploit
SCAM ALERT: The CrossCurve (EYWA) Bridge Exploit The Technical Breakdown (Simplified)
The Technical Breakdown (Simplified) Immediate Action Required
Immediate Action Required ShieldGuard Learn: Prevention & Due Diligence
ShieldGuard Learn: Prevention & Due Diligence