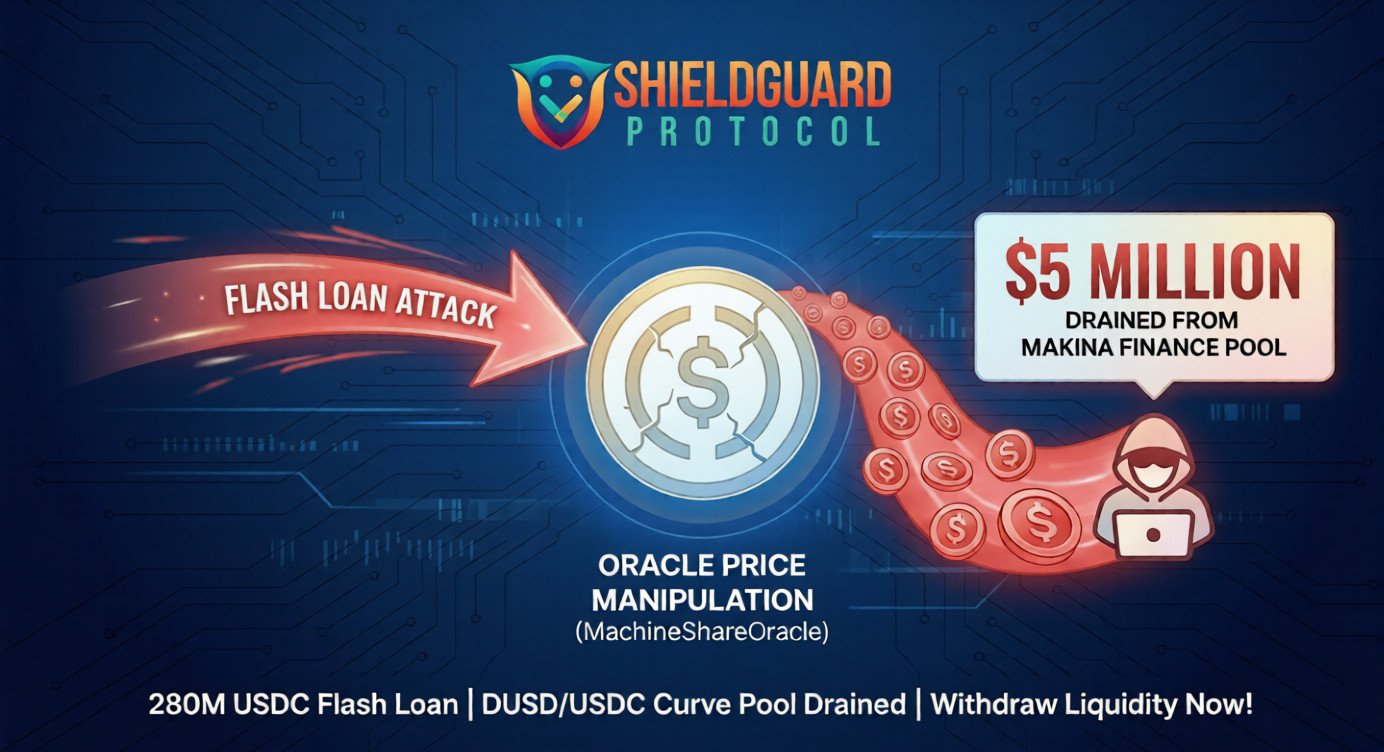
Alert: The $5 Million “Flash Loan” Exploit (Anatomy of the Makina Finance Attack)
Category: ShieldGuard Learn / Scam Prevention & Education
Risk Level: 🔴 Critical / Active Threat
The Incident
On Tuesday, January 20, 2026, the DeFi protocol Makina Finance was hit by a sophisticated exploit resulting in a loss of approximately $5 Million.
This was not a phishing link or a stolen password. It was a Flash Loan Attack—a technique where an attacker borrows hundreds of millions of dollars for mere seconds to manipulate the market and drain a protocol’s funds.
Here is the breakdown of how it happened, and why “Oracle Manipulation” is one of the biggest risks in DeFi.
1. The Attack: How It Happened
Security firms CertiK and PeckShield have confirmed the attack flow. The hacker did not use their own money; they used the protocol’s own mechanics against it.
- Step 1: The “Infinite” Loan
The attacker used a Flash Loan to borrow a staggering 280 Million USDC.
(Note: A Flash Loan allows you to borrow unlimited funds without collateral, as long as you pay it back in the same transaction block.)
- Step 2: The Price Manipulation
With this massive pile of cash, the attacker targeted Makina’s pricing system, known as the “MachineShareOracle.” By flooding the market with the borrowed funds, they artificially skewed the price of the assets Makina uses to calculate value.
- Step 3: The Drain
Once the Oracle was reporting the wrong price (thinking the assets were worth more/less than reality), the attacker exploited the DUSD/USDC Curve Pool. They traded against the pool at the “fake” price, extracting roughly $5 Million in profit.
- Step 4: The Getaway
The attacker repaid the 280 Million USDC loan and vanished. The entire robbery took less than 15 seconds (one block).
2. The Concept: What is “Oracle Manipulation”?
To understand this hack, imagine you walk into a grocery store.
- The Setup: You borrow $10 million from a bank for 10 seconds.
- The Trick: You use that $10 million to buy all the apples in the city, driving the price of an apple from $1 to $1,000.
- The Profit: You run to the grocery store (which checks the city price) and sell your single apple to them for $1,000.
- The Exit: You return the apples to the market (price crashes back to $1) and pay back the bank. You kept the profit from the store.
This is exactly what happened to Makina Finance. Their “Oracle” (the store) trusted the manipulated market price.
3. Current Status & Aftermath
- Funds Location: The stolen funds are currently sitting in two wallets: one controlled by the attacker and another by an MEV Bot (a “front-running” bot that accidentally or intentionally captured part of the stolen funds).
- Team Response: As of this report, the Makina Finance team has not officially confirmed the loss. This silence is a major red flag during a crisis.
ShieldGuard Verdict: Protecting Yourself
This incident is a reminder that in DeFi, code is law, but code can be tricked.
1. Avoid Protocols with “Thin” Liquidity
If a protocol relies on a pricing Oracle that can be manipulated by a single loan, it is unsafe. Always check if a project uses Chainlink or decentralized oracles, rather than their own internal price feeds.
2. The “Silence” Signal
If a protocol you are invested in suffers an exploit and the team goes silent for hours, assume the worst. Withdraw liquidity immediately.
3. Action Plan
- If you have funds in Makina Finance or the DUSD/USDC Curve Pool, withdraw them now.
- Revoke any token approvals for Makina Finance contracts using a tool like Revoke.cash to prevent future drains.
Join ShieldGuard for Real-Time Security Alerts