🚨 SECURITY ALERT: The “Weak OTP” Brute Force Attack
The Threat:
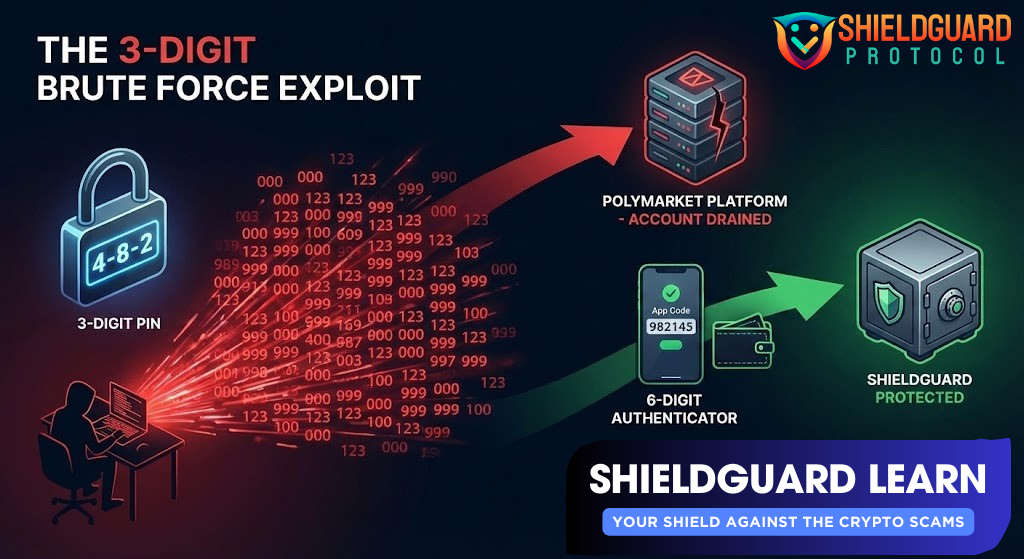
A specific vulnerability has been identified where attackers bypass 2FA not by stealing your code, but by guessing it. This recently targeted Polymarket users but can happen on any platform with weak security standards.
How It Works (The “Silent” Entry):
- The Trigger: The attacker enters your email on the login page.
- The Brute Force: The system sends you a code (e.g., “4-8-2”). Because the code is short (3-4 digits), the attacker’s bot tries every combination from 000 to 999 instantly.
- The Bypass: The system accepts the correct guess, and the attacker is logged in.
- The Result: You receive “Login Attempt” emails but ignore them (thinking you are safe because you didn’t click), while your account is being drained in the background.
🛡️ ShieldGuard Defense Guidelines:
- The “Unsolicited OTP” Rule: If you receive a login code (OTP) via email/SMS that you did not request, assume your account is under active brute-force attack.
- Immediate Action: Do not just ignore the email. Immediately log in (from a secure device) and change your password or withdraw funds if the platform allows “passwordless” login via email only.
- Hardware Over Email: Never rely solely on “Email Login” (Magic Links/OTPs) for holding crypto. Always use a Web3 Wallet (Metamask/Phantom) protected by a Ledger or Trezor. Email is the weakest link.
- Platform Vetting: If a financial platform uses 3-digit or 4-digit codes for security, withdraw immediately. This is below industry standards (minimum 6 digits required).
⚠️ Lesson:
“Not clicking the link” is not enough if the lock on the door is weak. Security is only as strong as the platform’s weakest code.
Stay Shielded. Verify Everything.