Phishing Alert: The “Ledger” Breach Aftershock
(Why You Are Receiving Personalized Scam Emails Today)
Threat Level: Critical
Executive Summary
A massive secondary wave of targeted phishing attacks is hitting cryptocurrency users today, January 12, 2026. This campaign is a direct “aftershock” of the data breach that occurred on January 5th, involving one of Ledger’s third-party payment processors.
Unlike generic spam, these emails are dangerous because they are highly personalized. The attackers are using stolen database records—including full names and email addresses—to craft messages that look 100% authentic.1
The Narrative: Scammers are weaponizing the recent news cycle, claiming that your device is vulnerable to the “Truebit Exploit” (a real event) to trick you into downloading fake firmware.
1. The Anatomy of the Attack
The attackers are combining Fear with Familiarity. By using your real name and referencing a verified industry hack, they bypass your natural skepticism.
The Email:
- Subject Line: “Urgent: Security Update Required for [Your Name]” or “Ledger Live: Firmware Vulnerability Patch.”
- The Hook: The email addresses you personally:
“Hello John, our security team has detected that your current Ledger Live version is vulnerable to the recent Truebit Protocol exploit. You must update your firmware immediately to secure your assets.”
Why it works:
- It uses your real name (stolen in the breach).
- It cites a real, trending security event (Truebit) to add credibility.
- It creates artificial urgency (“Update immediately”).
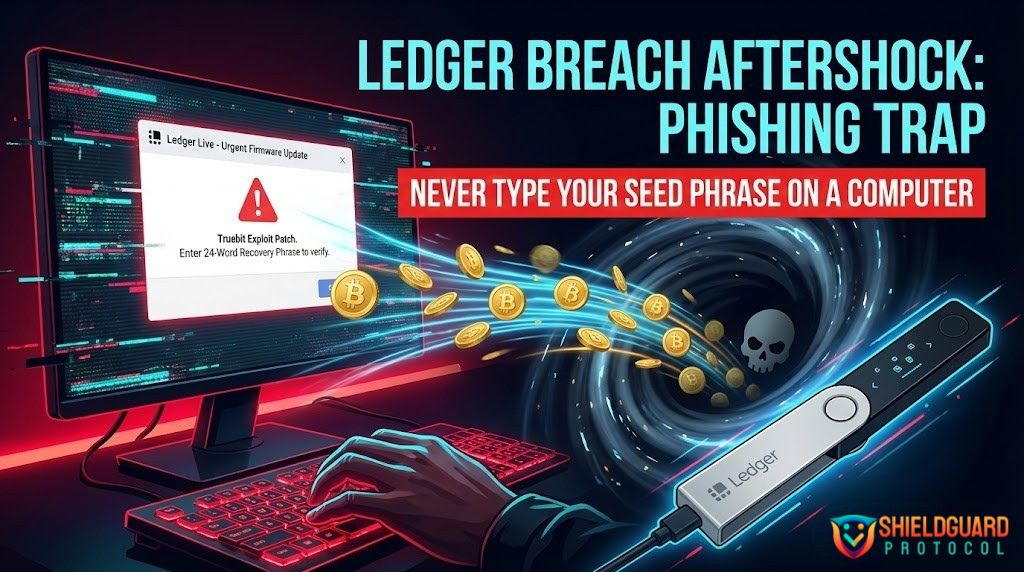
2. The Technical Trap: Fake Ledger Live
If you click the “Update Now” link, you are redirected to a clone website that perfectly mimics the official Ledger download page.
The Malware:
The file you download is not an update. It is a modified version of the Ledger Live application.
- The UI: It looks identical to the real app.
- The Trigger: When you open it, a pop-up appears: “Device Synchronization Failed. Please enter your 24-word Recovery Phrase to verify ownership.”
The Kill:As soon as you type your 24 words into your computer keyboard, the script sends them directly to the attacker’s server. Your wallet is drained seconds later.
3. The ShieldGuard Defense Protocols
Hardware wallets are the gold standard of security, but they have one fatal weakness: The User. The device cannot protect you if you give away the key.
Rule #1: The Golden Law
There is only one place you ever enter your 24-word seed phrase: The tiny physical screen of the Ledger device itself.
- NEVER type your seed phrase into a computer keyboard.
- NEVER take a photo of it.
- NEVER save it in a text file or cloud storage.
If an app on your computer asking for your seed phrase, it is malware. No exceptions.
Rule #2: Firmware Logic
Ledger devices are designed to be “cold.”2 They do not need emergency internet updates to stop a blockchain hack.
- Real firmware updates are only available inside the official Ledger Live app (the one already installed on your PC), never via an email link.
Rule #3: Ignore the Name
Just because an email knows your name, does not mean it is safe. In the age of data breaches, your name and email are public knowledge to hackers. Trust the Source, not the Salutation.
Conclusion
The scammers are betting that panic will make you forget the basics. They are using the Truebit news against you.
Take a deep breath. Your Ledger is safe—as long as your seed phrase stays offline.
Scammers never sleep, and neither does our protocol. Stay paranoid, stay shielded.
🛡️ About ShieldGuard Protocol
ShieldGuard is the first vertically integrated Web3 security ecosystem, combining AI-driven scam prevention, the ShieldGuard Mobile App, and ShieldLabs Incubator to protect the next generation of crypto users.
Stay Shielded:
🌐 Website: shieldguard.io
🐦 X (Twitter): @Shieldguardio
📄 Docs & Audit: docs.shieldguard.io
⚠️ Disclaimer: This content is for educational purposes only and does not constitute financial advice. Cryptocurrency investments carry high risk.3 Always do your own research (DYOR) before interacting with any protocol.