Case Study: The “Perfect” Email Spoof – How We Exposed a Fake Upbit Ring (And Why Every User is at Risk)
Author: Ajayakumar K, CEO ShieldGuard Protocol
Executive Summary: This week, ShieldGuard Protocol dismantled a high-level scam ring impersonating Upbit Exchange. While they targeted us for a “Listing Collaboration,” our investigation revealed a vulnerability that threatens every single crypto user, not just project founders.
The attackers possess the ability to spoof official Upbit email addresses. If they can email us as partnership@upbit.com, they can email you as support@upbit.com to steal your funds.
1. The Trap: The “Listing” Pitch The attackers (operating via Telegram handles @jkelly_dev, @enkze, and a fake LinkedIn profile “Luennis L Yun: https://www.linkedin.com/in/luennis-l-yun-09739a121/“) approached us with a listing collaboration offer. Instead of rejecting them immediately, we engaged. We tested their capabilities by negotiating for an Initial Exchange Offering (IEO).
- The Bluff: They immediately agreed to a $6M raise via private rounds—a classic sign of a scammer promising the world to get a fee.
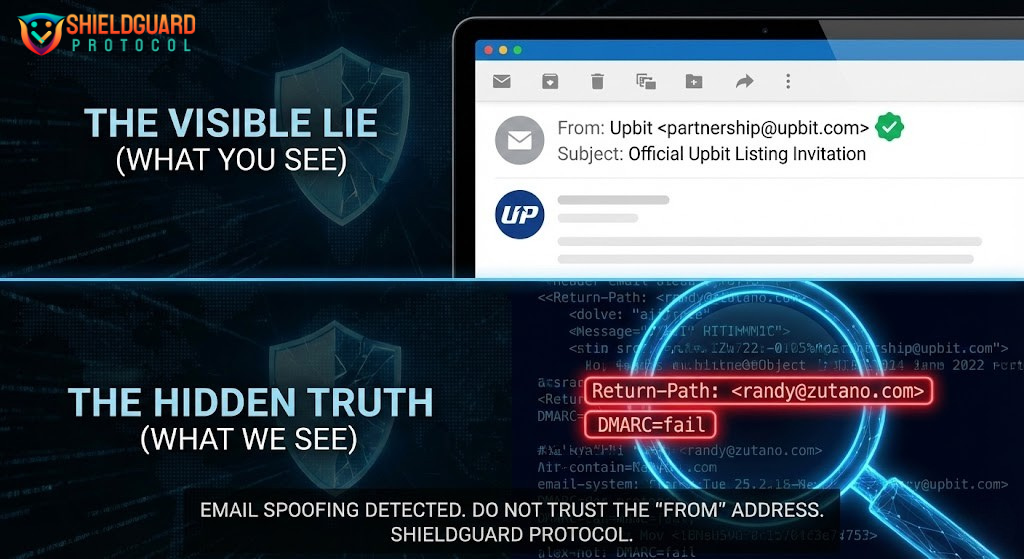
2. The Weapon: Email Spoofing To prove their identity, they sent us an official invitation. On the surface, it looked perfect. The sender field read: partnership@upbit.com. Most people stop checking there. We didn’t.
3. The Forensic Breakdown (The “Smoking Gun”) We pulled the Email Headers (the hidden digital passport of the message). The lie collapsed instantly:
- Display Name: Upbit
- The Trap:
From: partnership@upbit.com - The REAL Sender (Return-Path):
randy@zutano[.]com - The Security Failure:
DMARC=fail
Analysis: The attackers compromised an email server belonging to a clothing brand (“Zutano”) and used it to mask their identity as Upbit.
4. Why This Matters to YOU (The Retail User) This is not just a B2B threat. If these scammers can spoof partnership@upbit.com to trick a CEO, they can easily spoof help@upbit.com or security@upbit.com to trick YOU.
Imagine receiving an email that looks exactly like it comes from Upbit, telling you:
“Your account is compromised. Click here to reset your password.”
Because the email address looks real, you might click. That is how wallets get drained.
5. Our Call to Action
- To Upbit: @Official_Upbit We urge you to implement stricter DMARC policies (p=reject). Currently, your domain allows spoofed emails to land in inboxes. This is a massive security gap.
- To Users: Never trust the “From” address. If an exchange emails you, do not click links. Go to the app/website manually.
- To Founders: If a listing offer comes via Telegram first, it is a scam. Period.
Conclusion: We played along to expose their methods. ShieldGuard Protocol is built to see what the human eye misses.